Why MDR is the Hottest Acronym in Security
Round-the-clock threats and a lack of in-house expertise have MSPs turning to security vendors for services on top of software and hardware.
In cybersecurity, a market dripping with acronyms, “MDR” just may be the hottest one there is right now.
In the last few weeks alone, WatchGuard has rolled out a managed detection and response solution as has SonicWall via its acquisition of Solutions Granted. Go back a bit further and you have ThreatDown (better known until recently as Malwarebytes for Business) adding an EDR/MDR hybrid service and Sophos supplementing its briskly-selling MDR offering with an incident response retainer service.
The question all of this activity inevitably inspires, though, is why?
Well, to borrow very loosely from Mike Tyson, everyone has a plan until they’re kicked in the face. And MSPs?
“They’re starting to get kicked in the face more,” says Matt Lee, senior director of security and compliance at cloud distributor Pax8. Indeed, 46% of their SMB clients have experienced a ransomware attack this year, according to recent data from OpenText, and ransomware isn’t the only threat worth worrying about. That has more and more MSPs looking for a new and better plan than their old one, which was basically to assemble a stack of security tools and manage it themselves.
“What we’ve heard from that community is that they need help,” says Andrew Young, WatchGuard’s chief product officer.
To be clear, the problem here isn’t the tools. There are great tools of all sorts out there. Maybe too many, in fact, and too great. Consider EDR tools alone, suggests Brian Kane, global director of MSP programs at ThreatDown, and a former MSP himself.
“When I hear EDR, here’s what I hear: a lot more alerts,” he says. “Who’s looking at that? A tier 1, maybe a tier 2 tech. Those aren’t trained eyes to manage those things.”
Good luck hiring and retaining trained eyes too. The world has 5.5 million security professionals at present, according to the latest Cybersecurity Workforce Study from ISC2, and needs 4 million more to keep pace with requirements.
Hence the dilemma most MSPs find themselves in at present. Drowning around the clock in threats and information about those threats from their tools, they lack the skills and people to interpret and act on all that input.
“That’s the gap,” Lee (pictured) says. “It’s an expertise gap. It’s having the judgment, and if not the judgment, the ability to scale that judgment.”
And don’t forget one last unavoidable issue, adds Huntress CEO Kyle Hanslovan. Compliance mandates, cybersecurity frameworks, and cyberinsurers increasingly require the kind of round-the-cloud vigilance many MSPs can’t provide.
“It’s not just do you have the technology,” he says. “It’s can you do attestation that you’re managing it and that you’re doing it 24x7.”
All of which explains why Canalys expects global MDR spending to climb 34.5% this year to $3.1 billion. Sum it up, in fact, and it’s easy to see why MDR is fast becoming not a useful service but a mandatory one in every MSP’s security stack, and every security vendor’s portfolio.
And the winner is…
Which leads to another question: which MDR solution should an MSP use? Because the faster such services proliferate, the harder it is to separate fact from hype in their often similar marketing.
“They’ll say, ‘we provide world-class talent and manage groundbreaking technology to deliver you affordable security at scale,’” Hanslovan (pictured) observes. “[MSPs] need to be able to ask the questions that can validate is this marketing fluff or can they actually deliver that service?”
Hanslovan, in a recent presentation at ConnectWise’s IT Nation Connect event, suggested 16 such questions, starting with who’s behind the solution and do they work night shifts?
“There are vendors that promise 24x7 [coverage] that are a 10-person company,” Hanslovan notes. “You can do math and it’s easy to determine that that’s not legitimate.”
And if they have more than 10 people on staff? Who are those people, Hanslovan asks, what are their accomplishments, and how have they proven themselves?
“Usually folks will say, ‘well, we have this many people with a degree or this many people with these certificates,’” he observes. What really matters, though, is whether or not those people have played documented roles responding to publicly reported incidents, or how often they present research at conferences like Black Hat and DEF CON.
Lee, for his part, suggests steering clear of anyone who promises to prevent or detect everything dangerous. “Those are claims that aren’t realistic in cybersecurity,” he says. Vendors that say they help partners minimize the impact of incidents and respond to them swiftly are more trustworthy.
Young, of WatchGuard, cites additional criteria of particular importance to MSPs that informed the design of its new MDR offering, like how simple is the service to use? At WatchGuard, he continues, “we do all the threat hunting, monitoring, the reporting, and then incident response to the point of isolation.” Then it provides a detailed, do-it-yourself remediation playbook.
“We do it in such a way that a mainstream MSP, not an MSSP, can use it and leverage it to go through the process,” Young says.
Pay close attention to how closely the service aligns with your business model, he adds, and not just in terms of how you pay for it. WatchGuard, for example, allows MSPs to white label its solution if they wish.
“We kind of make them the hero,” Young says. “They can position it as their own MDR service out to their customer.”
Above all, Hanslovan concludes, keep asking questions like those. Forever. Executives and security analysts come and go. R&D budgets rise and fall.
“Any of these vendors could be great today and rough tomorrow,” Hanslovan observes.
New podcast
I’m co-hosting a new podcast! Click the graphic above or here to learn more and subscribe.
Put your trust in zero trust, says Veeam
In the earliest days of Veeam’s existence, way back in 2006, the first person co-founders Ratmir Timashev and Andrei Baronov hired was a developer (still on staff) who went on to write the first version of what’s since become the company’s widely-used data protection platform.
One of his early design decisions, explains Rick Vanover, Veeam’s senior director of product strategy, was to embrace a bring-your-own storage architecture that freed him from having to worry about that part of the solution.
“He didn’t want to have to be a storage admin,” Vanover (pictured) says. “He wanted to be a coder.”
Separating software from storage turned out to have other benefits, though. For one thing, it gives buyers freedom to choose from a variety of storage platforms. For another, it keeps that storage safer by making it much harder for an attacker who compromises Veeam’s code to destroy a user’s data as well.
It would be another three years, in 2009, until Forrester analyst John Kindervag first coined the term “zero trust” to describe environments in which, among other things, software has no inherent faith in the integrity of storage and storage has no inherent confidence in the integrity of software.
And it would be another 14 years—this week to be precise—before Veeam, in partnership with Numberline Security, would publish a white paper on Zero Trust Data Resilience (ZTDR), a model for building zero-trust data protection solutions that isolate backup management systems from their storage tiers.
Based on CISA’s Zero Trust Maturity Model, ZTDR offers guidelines and a reference architecture inspired by five key principles: least privilege access, immutability, operational simplicity, system resilience (via network segmentation, MFA, and the like), and “proactive validation” (as in verifying backups and scanning them for malware before restoring them).
According to Vanover, Object First, the Veeam-specific backup storage vendor we’ve written about before here at Channelholic, proposed and co-authored the ZTDR paper.
“The ZTDR architecture and maturity model provides the channel a practical way to advise customers, assess their maturity, and chart a path leveraging technology and process to significantly better backup data security,” says Anthony Cusimano, Object First’s chief evangelist and director of technical marketing. “It’s an advantageous way to bring IT and security teams together to improve an organization’s overall security posture.”
The goal, adds Vanover, is to show readers that, fundamentally, zero trust isn’t a product. “It’s an idea.”
Though not necessarily a simple one. “It does get technical,” says Vanover of the ZTDR paper. “I’m not going to beat around the bush.” That said, most readers will have the know-how to implement its recommendations, he continues, adding that those who don’t should get help from a partner rather than ignore the issue and hope for the best.
“That’s a 911 call waiting to happen,” Vanover says.
Crypto MRR?
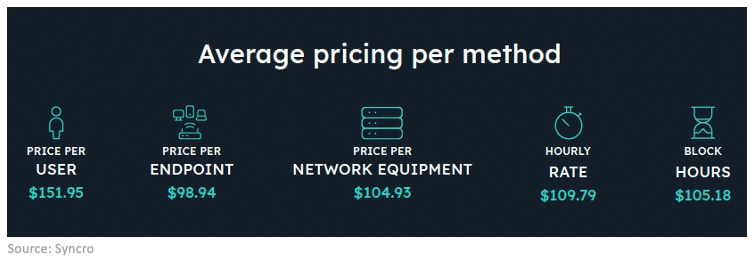
Syncro, which published interesting research in April about where MSPs go for business insights, has equally interesting research out this week on managed services pricing trends. Here’s what your peers in the U.S.-only sample are charging for their work right now:
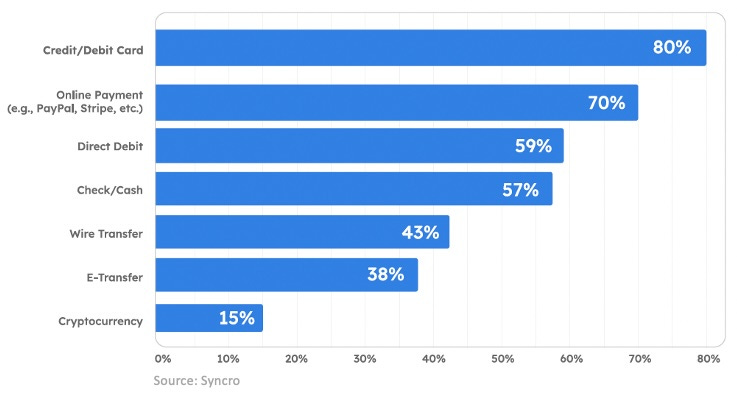
I encourage you to dive into the study yourself for additional nuggets, but wonder what you think about this chart on how MSPs accept payment:
Look closely. Can it be true that 15% of MSPs accept payment in cryptocurrency? That’s a small number in absolute terms, but bigger than I would have guessed.
Forgive all the promos this week
I can’t help myself though…
Behind the (ConnectWise) deal
Did you know that private equity heavyweight Thoma Bravo has a podcast? Called Behind the Deal and now in its second season, the show draws on testimony from CEOs and Thoma Bravo managing partners to explain how one of the firm’s acquisitions came about.
I’ve been listening regularly since the series debuted for two reasons. First, it’s brilliant marketing. Say what you will about private equity, you only need to hear an episode or two before the obvious rapport between the deal-makers featured each week has you imagining an acquired company exec somewhere turning to their PE advisors and asking, Jerry Maquire style, “why don’t we have that kind of relationship?”
Second, I’ve been eagerly awaiting an episode dedicated to a Thoma Bravo holding that I write about. My wait is finally over. The latest episode, which dropped yesterday, is all about the investor’s 2019 acquisition of ConnectWise. Featuring a conversation between Thoma Bravo partner Mike Hoffman and ConnectWise CEO Jason Magee, the show is recommended listening. Among other things, you’ll learn that:
ConnectWise has roughly tripled its top line since the sale. “We’re not at a billion dollars yet, but I’d say well on its way,” Hoffman reports at about the 10:45 mark.
Earnings growth since 2019 has been “really impressive” as well, Hoffman says shortly afterwards, “and put the company in a really, really great position.”
ConnectWise Co-Founder Arnie Bellini wavered during the negotiating process about whether or not to step down as CEO.
He did so ultimately and now, per reporting by Jessica C. Davis in ChannelE2E, is about three months away from being released from his non-compete agreement.
And what then? Call me, Arnie. I’ve got a podcast of my own these days to talk about it on, and it’s been way too long since we’ve spoken.
Also worth noting
Move over, AWS! Hewlett Packard Enterprise is partnering with NVIDIA on artificial intelligence too.
Trend Micro now offers AI-powered assistance to overwhelmed security analysts.
TD SYNNEX partners can now use Intel’s Geti platform to produce AI training models.
More from TD SYNNEX: Michael Urban, its Americas president, will exit the company March 1st, two months after Patrick Zammit officially becomes COO.
Pax8 has signed an expanded distribution agreement with EDR big shot SentinelOne.
ManageEngine’s SIEM now features a new “dual-layer” machine learning-based threat detection system.
Nothing draws applause from MSPs more quickly during product roadmap presentations than adding dark mode, so cue the applause for Keeper Security.
I’m late to this one: N-able’s Cove data protection solution now backs up and recovers teams, members, settings, and files in Microsoft Teams.
Jim Elder is the new VP of global pathways at data erasure vendor Blancco.